-- David Wheeler
ARM introduces its virtualization extensions to its architecture from ARMv7. VMM thus can virtualize the entire instruction set by implementing trap-and-emulate model with hardware instead of software. ARM virtualization extensions include following:
- Hypervisor execution mode, a higher priority mode than supervisor mode.
- Virtual interrupts
- System MMU, supporting multiple translation context for multiple DMA masters, two stage address translation and hardware acceleration and abstraction
HYP mode
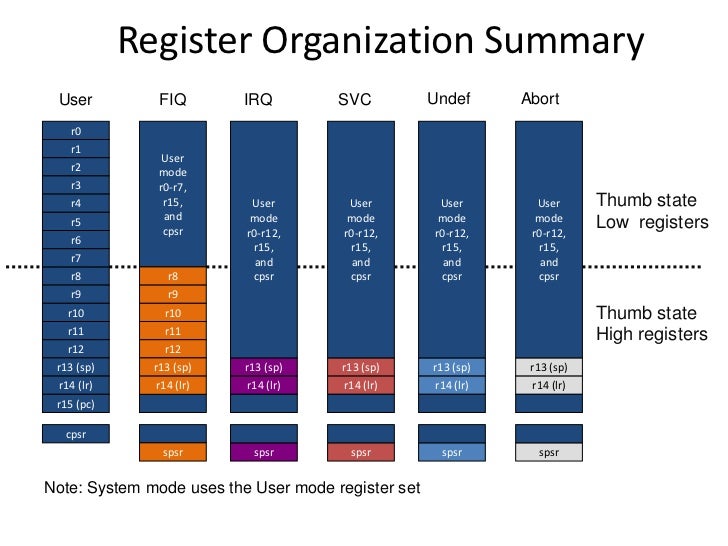
ARMv7 introduces new privilege level and new HYP mode for hypervisor execution. HYP mode has higher privilege than SVC mode. The introduction of new HYP mode allows most of sensitive instructions native-run on non-secure PL1 without trap-and-emulation and the rest, e.g. guest's Load/Store, will be trapped into HYP mode. HYP mode can only enabled by software running from secure state.With virtualization extension, the sensitive instructions which can't be execute natively will be trapped automatically when running in PL1. Hypervisor Syndrome Register (HSR), part of virtualization extension, preserves the information, e.g. reason of entry. HVC is an instruction which helps entering HYP mode from guest OS.
Hypervisor also has its own vector table. The base address of HYP mode's vector table is saved in HVBAR, which is accessible only from monitor or HYP mode. VBAR saves base address of PL0/1 vector table.
Memory Virtualization
Armv7 also introduces 2-Stage Address Translation where Stage 1 maps virtual address (VA) to an Intermediate Physical Address (IPA) and Stage 2 maps the IPA to Physical Address (PA). Guest OS maintains Stage 1 page tables and hypervisor take whole control of Stage 2.
The Translation Lookaside Buffer (TLB) entry also include virtual machine ID tag (VMID) such that TLBs do not require explicit invalidation when changing among virtual machines.
System MMU
Stage 1 SMMU translation enables a DMA capable device to operate on fragmented physical memory, which is simpler and more efficient than software appoach DMA scatter-gather. It also enables devices that can't access full range of memory such as 16 or 24 bit devices on 32 bit architecture to access any address of the system without help from bounce buffers.
Stage 2 SMMU translation removes the need for hypervisor to maintain shadow tables. Since Guest OS can only access DMA capable devices at IPA level, DMA attack is prevented from corrupting memory of another Guest OS.
Interrupt Virtualization
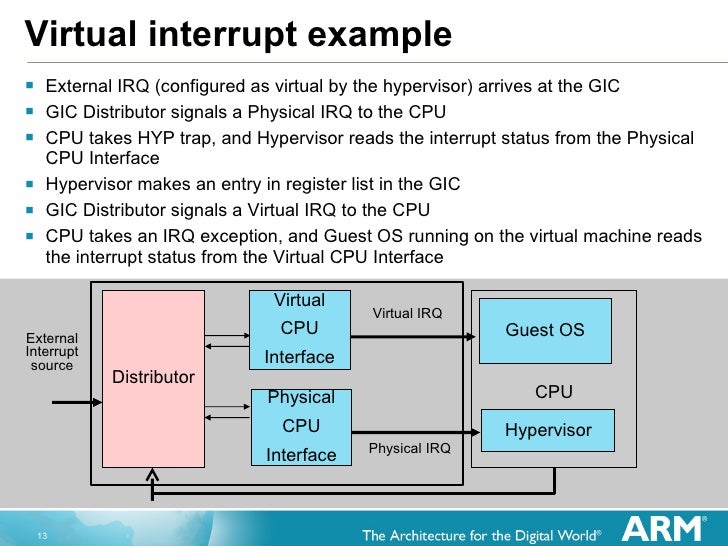
Generic Interrupt Controller (GIC) is the only interrupt controller in ARM architecture. Interrupt distributor, can be configured at boot time, saves the information of interrupt routing. Virtualization Extensions provides a separate register set for virtual interrupts such that ISR of Guest OS can interact directly with virtual GIC. Hypervisor can configure interrupt in Hypervisor Configuration Register (HCR) to generate a hypervisor trap and to deliver an interrupt to a CPU running in virtual process.
References
- https://linux.globallogic.com/materials2017/presentations/Main%20stage/Julien%20Grall%20Hypervisors%20on%20ARM%20Overview%20and%20Design%20choices.pdf
- https://www.slideshare.net/xen_com_mgr/hardware-accelerated-virtualization-in-the-arm-cortex-processors
- http://www.csd.uoc.gr/~hy428/reading/vm-support-ARM-may20-2014.pdf
- http://www.hotchips.org/wp-content/uploads/hc_archives/hc22/HC22.23.220-1-Brash-ARMv7A.pdf
- https://blog.linuxplumbersconf.org/2012/wp-content/uploads/2012/09/2012-lpc-arm-zyngier.pdf
- http://www.cs.nthu.edu.tw/~ychung/slides/Virtualization/VM-Lecture-7-2-Hardware%20support-ARM.pptx
- https://www.slideshare.net/jserv/embedded-hypervisor-for-arm